1.des算法源代码
2.openssl å¦ä½ä½¿ç¨
3.什么是国密算法?
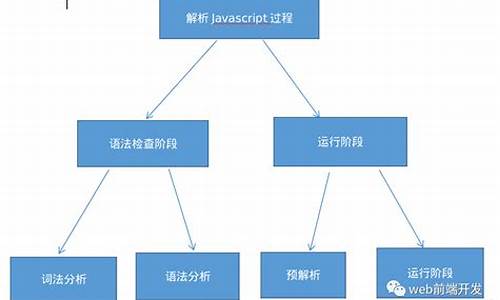
des算法源代码
des.h文件:
#ifndef CRYPTOPP_DES_H
#define CRYPTOPP_DES_H
#include "cryptlib.h"
#include "misc.h"
NAMESPACE_BEGIN(CryptoPP)
class DES : public BlockTransformation
{
public:
DES(const byte *userKey, CipherDir);
void ProcessBlock(const byte *inBlock, byte * outBlock) const;
void ProcessBlock(byte * inoutBlock) const
{ DES::ProcessBlock(inoutBlock, inoutBlock);}
enum { KEYLENGTH=8, BLOCKSIZE=8};
unsigned int BlockSize() const { return BLOCKSIZE;}
protected:
static const word Spbox[8][];
SecBlock<word> k;
};
class DESEncryption : public DES
{
public:
DESEncryption(const byte * userKey)
: DES (userKey, ENCRYPTION) { }
};
class DESDecryption : public DES
{
public:
DESDecryption(const byte * userKey)
: DES (userKey, DECRYPTION) { }
};
class DES_EDE_Encryption : public BlockTransformation
{
public:
DES_EDE_Encryption(const byte * userKey)
: e(userKey, ENCRYPTION), d(userKey + DES::KEYLENGTH, DECRYPTION) { }
void ProcessBlock(const byte *inBlock, byte * outBlock) const;
void ProcessBlock(byte * inoutBlock) const;
enum { KEYLENGTH=, BLOCKSIZE=8};
unsigned int BlockSize() const { return BLOCKSIZE;}
private:
DES e, d;
};
class DES_EDE_Decryption : public BlockTransformation
{
public:
DES_EDE_Decryption(const byte * userKey)
: d(userKey, DECRYPTION), e(userKey + DES::KEYLENGTH, ENCRYPTION) { }
void ProcessBlock(const byte *inBlock, byte * outBlock) const;
void ProcessBlock(byte * inoutBlock) const;
enum { KEYLENGTH=, BLOCKSIZE=8};
unsigned int BlockSize() const { return BLOCKSIZE;}
private:
DES d, e;
};
class TripleDES_Encryption : public BlockTransformation
{
public:
TripleDES_Encryption(const byte * userKey)
: e1(userKey, ENCRYPTION), d(userKey + DES::KEYLENGTH, DECRYPTION),
e2(userKey + 2*DES::KEYLENGTH, ENCRYPTION) { }
void ProcessBlock(const byte *inBlock, byte * outBlock) const;
void ProcessBlock(byte * inoutBlock) const;
enum { KEYLENGTH=, BLOCKSIZE=8};
unsigned int BlockSize() const { return BLOCKSIZE;}
private:
DES e1, d, e2;
};
class TripleDES_Decryption : public BlockTransformation
{
public:
TripleDES_Decryption(const byte * userKey)
: d1(userKey + 2*DES::KEYLENGTH, DECRYPTION), e(userKey + DES::KEYLENGTH, ENCRYPTION),
d2(userKey, DECRYPTION) { }
void ProcessBlock(const byte *inBlock, byte * outBlock) const;
void ProcessBlock(byte * inoutBlock) const;
enum { KEYLENGTH=, BLOCKSIZE=8};
unsigned int BlockSize() const { return BLOCKSIZE;}
private:
DES d1, e, d2;
};
NAMESPACE_END
#endif
des.cpp文件:
// des.cpp - modified by Wei Dai from:
/*
* This is a major rewrite of my old public domain DES code written
* circa , which in turn borrowed heavily from Jim Gillogly's
* public domain code. I pretty much kept my key scheduling code, but
* the actual encrypt/decrypt routines are taken from from Richard
* Outerbridge's DES code as printed in Schneier's "Applied Cryptography."
*
* This code is in the public domain. I would appreciate bug reports and
* enhancements.
*
* Phil Karn KA9Q, karn@unix.ka9q.ampr.org, August .
*/
#include "pch.h"
#include "misc.h"
#include "des.h"
NAMESPACE_BEGIN(CryptoPP)
/* Tables defined in the Data Encryption Standard documents
* Three of these tables, the initial permutation, the final
* permutation and the expansion operator, are regular enough that
* for speed, we hard-code them. They're here for reference only.
* Also, the S and P boxes are used by a separate program, gensp.c,
* to build the combined SP box, Spbox[]. They're also here just
* for reference.
*/
#ifdef notdef
/* initial permutation IP */
static byte ip[] = {
, , , , , , , 2,
, , , , , , , 4,
, , , , , , , 6,
, , , , , , , 8,
, , , , , , 9, 1,
, , , , , , , 3,
, , , , , , , 5,
, , , , , , , 7
};
/* final permutation IP^-1 */
static byte fp[] = {
, 8, , , , , , ,
, 7, , , , , , ,
, 6, , , , , , ,
, 5, , , , , , ,
, 4, , , , , , ,
, 3, , , , , , ,
, 2, , , , , , ,
, 1, , 9, , , ,
};
/* expansion operation matrix */
static byte ei[] = {
, 1, 2, 3, 4, 5,
4, 5, 6, 7, 8, 9,
8, 9, , , , ,
, , , , , ,
, , , , , ,
, , , , , ,
, , , , , ,
, , , , , 1
};
/* The (in)famous S-boxes */
static byte sbox[8][] = {
/* S1 */
, 4, , 1, 2, , , 8, 3, , 6, , 5, 9, 0, 7,
0, , 7, 4, , 2, , 1, , 6, , , 9, 5, 3, 8,
4, 1, , 8, , 6, 2, , , , 9, 7, 3, , 5, 0,
, , 8, 2, 4, 9, 1, 7, 5, , 3, , , 0, 6, ,
/* S2 */
, 1, 8, , 6, , 3, 4, 9, 7, 2, , , 0, 5, ,
3, , 4, 7, , 2, 8, , , 0, 1, , 6, 9, , 5,
0, , 7, , , 4, , 1, 5, 8, , 6, 9, 3, 2, ,
, 8, , 1, 3, , 4, 2, , 6, 7, , 0, 5, , 9,
/* S3 */
, 0, 9, , 6, 3, , 5, 1, , , 7, , 4, 2, 8,
, 7, 0, 9, 3, 4, 6, , 2, 8, 5, , , , , 1,
, 6, 4, 9, 8, , 3, 0, , 1, 2, , 5, , , 7,
1, , , 0, 6, 9, 8, 7, 4, , , 3, , 5, 2, ,
/* S4 */
7, , , 3, 0, 6, 9, , 1, 2, 8, 5, , , 4, ,
, 8, , 5, 6, , 0, 3, 4, 7, 2, , 1, , , 9,
, 6, 9, 0, , , 7, , , 1, 3, , 5, 2, 8, 4,
3, , 0, 6, , 1, , 8, 9, 4, 5, , , 7, 2, ,
/* S5 */
2, , 4, 1, 7, , , 6, 8, 5, 3, , , 0, , 9,
, , 2, , 4, 7, , 1, 5, 0, , , 3, 9, 8, 6,
4, 2, 1, , , , 7, 8, , 9, , 5, 6, 3, 0, ,
, 8, , 7, 1, , 2, , 6, , 0, 9, , 4, 5, 3,
/* S6 */
, 1, , , 9, 2, 6, 8, 0, , 3, 4, , 7, 5, ,
, , 4, 2, 7, , 9, 5, 6, 1, , , 0, , 3, 8,
9, , , 5, 2, 8, , 3, 7, 0, 4, , 1, , , 6,
4, 3, 2, , 9, 5, , , , , 1, 7, 6, 0, 8, ,
/* S7 */
4, , 2, , , 0, 8, , 3, , 9, 7, 5, , 6, 1,
, 0, , 7, 4, 9, 1, , , 3, 5, , 2, , 8, 6,
1, 4, , , , 3, 7, , , , 6, 8, 0, 5, 9, 2,
6, , , 8, 1, 4, , 7, 9, 5, 0, , , 2, 3, ,
/* S8 */
, 2, 8, 4, 6, , , 1, , 9, 3, , 5, 0, , 7,
1, , , 8, , 3, 7, 4, , 5, 6, , 0, , 9, 2,
7, , 4, 1, 9, , , 2, 0, 6, , , , 3, 5, 8,
2, 1, , 7, 4, , 8, , , , 9, 0, 3, 5, 6,
};
/* -bit permutation function P used on the output of the S-boxes */
static byte pi[] = {
, 7, , ,
, , , ,
1, , , ,
5, , , ,
2, 8, , ,
, , 3, 9,
, , , 6,
, , 4,
};
#endif
/* permuted choice table (key) */
static const byte pc1[] = {
, , , , , , 9,
1, , , , , , ,
, 2, , , , , ,
, , 3, , , , ,
, , , , , , ,
7, , , , , , ,
, 6, , , , , ,
, , 5, , , , 4
};
/* number left rotations of pc1 */
static const byte totrot[] = {
1,2,4,6,8,,,,,,,,,,,
};
/* permuted choice key (table) */
static const byte pc2[] = {
, , , , 1, 5,
3, , , 6, , ,
, , , 4, , 8,
, 7, , , , 2,
, , , , , ,
, , , , , ,
, , , , , ,
, , , , ,
};
/* End of DES-defined tables */
/* bit 0 is left-most in byte */
static const int bytebit[] = {
,,,,,,,
};
/* Set key (initialize key schedule array) */
DES::DES(const byte *key, CipherDir dir)
: k()
{
SecByteBlock buffer(++8);
byte *const pc1m=buffer; /* place to modify pc1 into */
byte *const pcr=pc1m+; /* place to rotate pc1 into */
byte *const ks=pcr+;
register int i,j,l;
int m;
for (j=0; j<; j++) { /* convert pc1 to bits of key */
l=pc1[j]-1; /* integer bit location */
m = l & ; /* find bit */
pc1m[j]=(key[l>>3] & /* find which key byte l is in */
bytebit[m]) /* and which bit of that byte */
1 : 0; /* and store 1-bit result */}
for (i=0; i<; i++) { /* key chunk for each iteration */
memset(ks,0,8); /* Clear key schedule */
for (j=0; j<; j++) /* rotate pc1 the right amount */
pcr[j] = pc1m[(l=j+totrot[i])<(j<? : ) ? l: l-];
/* rotate left and right halves independently */
for (j=0; j<; j++){ /* select bits individually */
/* check bit that goes to ks[j] */
if (pcr[pc2[j]-1]){
/* mask it in if it's there */
l= j % 6;
ks[j/6] |= bytebit[l] >> 2;
}
}
/* Now convert to odd/even interleaved form for use in F */
k[2*i] = ((word)ks[0] << )
| ((word)ks[2] << )
| ((word)ks[4] << 8)
| ((word)ks[6]);
k[2*i+1] = ((word)ks[1] << )
| ((word)ks[3] << )
| ((word)ks[5] << 8)
| ((word)ks[7]);
}
if (dir==DECRYPTION) // reverse key schedule order
for (i=0; i<; i+=2)
{
std::swap(k[i], k[-2-i]);
std::swap(k[i+1], k[-1-i]);
}
}
/* End of C code common to both versions */
/* C code only in portable version */
// Richard Outerbridge's initial permutation algorithm
/*
inline void IPERM(word &left, word &right)
{
word work;
work = ((left >> 4) ^ right) & 0x0f0f0f0f;
right ^= work;
left ^= work << 4;
work = ((left >> ) ^ right) & 0xffff;
right ^= work;
left ^= work << ;
work = ((right >> 2) ^ left) & 0x;
left ^= work;
right ^= (work << 2);
work = ((right >> 8) ^ left) & 0xffff;
left ^= work;
right ^= (work << 8);
right = rotl(right, 1);
work = (left ^ right) & 0xaaaaaaaa;
left ^= work;
right ^= work;
left = rotl(left, 1);
}
inline void FPERM(word &left, word &right)
{
word work;
right = rotr(right, 1);
work = (left ^ right) & 0xaaaaaaaa;
left ^= work;
right ^= work;
left = rotr(left, 1);
work = ((left >> 8) ^ right) & 0xffff;
right ^= work;
left ^= work << 8;
work = ((left >> 2) ^ right) & 0x;
right ^= work;
left ^= work << 2;
work = ((right >> ) ^ left) & 0xffff;
left ^= work;
right ^= work << ;
work = ((right >> 4) ^ left) & 0x0f0f0f0f;
left ^= work;
right ^= work << 4;
}
*/
// Wei Dai's modification to Richard Outerbridge's initial permutation
// algorithm, this one is faster if you have access to rotate instructions
// (like in MSVC)
inline void IPERM(word &left, word &right)
{
word work;
right = rotl(right, 4U);
work = (left ^ right) & 0xf0f0f0f0;
left ^= work;
right = rotr(right^work, U);
work = (left ^ right) & 0xffff;
left ^= work;
right = rotr(right^work, U);
work = (left ^ right) & 0x;
left ^= work;
right = rotr(right^work, 6U);
work = (left ^ right) & 0xffff;
left ^= work;
right = rotl(right^work, 9U);
work = (left ^ right) & 0xaaaaaaaa;
left = rotl(left^work, 1U);
right ^= work;
}
inline void FPERM(word &left, word &right)
{
word work;
right = rotr(right, 1U);
work = (left ^ right) & 0xaaaaaaaa;
right ^= work;
left = rotr(left^work, 9U);
work = (left ^ right) & 0xffff;
right ^= work;
left = rotl(left^work, 6U);
work = (left ^ right) & 0x;
right ^= work;
left = rotl(left^work, U);
work = (left ^ right) & 0xffff;
right ^= work;
left = rotl(left^work, U);
work = (left ^ right) & 0xf0f0f0f0;
right ^= work;
left = rotr(left^work, 4U);
}
// Encrypt or decrypt a block of data in ECB mode
void DES::ProcessBlock(const byte *inBlock, byte * outBlock) const
{
word l,r,work;
#ifdef IS_LITTLE_ENDIAN
l = byteReverse(*(word *)inBlock);
r = byteReverse(*(word *)(inBlock+4));
#else
l = *(word *)inBlock;
r = *(word *)(inBlock+4);
#endif
IPERM(l,r);
const word *kptr=k;
for (unsigned i=0; i<8; i++)
{
work = rotr(r, 4U) ^ kptr[4*i+0];
l ^= Spbox[6][(work) & 0x3f]
^ Spbox[4][(work >> 8) & 0x3f]
^ Spbox[2][(work >> ) & 0x3f]
^ Spbox[0][(work >> ) & 0x3f];
work = r ^ kptr[4*i+1];
l ^= Spbox[7][(work) & 0x3f]
^ Spbox[5][(work >> 8) & 0x3f]
^ Spbox[3][(work >> ) & 0x3f]
^ Spbox[1][(work >> ) & 0x3f];
work = rotr(l, 4U) ^ kptr[4*i+2];
r ^= Spbox[6][(work) & 0x3f]
^ Spbox[4][(work >> 8) & 0x3f]
^ Spbox[2][(work >> ) & 0x3f]
^ Spbox[0][(work >> ) & 0x3f];
work = l ^ kptr[4*i+3];
r ^= Spbox[7][(work) & 0x3f]
^ Spbox[5][(work >> 8) & 0x3f]
^ Spbox[3][(work >> ) & 0x3f]
^ Spbox[1][(work >> ) & 0x3f];
}
FPERM(l,r);
#ifdef IS_LITTLE_ENDIAN
*(word *)outBlock = byteReverse(r);
*(word *)(outBlock+4) = byteReverse(l);
#else
*(word *)outBlock = r;
*(word *)(outBlock+4) = l;
#endif
}
void DES_EDE_Encryption::ProcessBlock(byte *inoutBlock) const
{
e.ProcessBlock(inoutBlock);
d.ProcessBlock(inoutBlock);
e.ProcessBlock(inoutBlock);
}
void DES_EDE_Encryption::ProcessBlock(const byte *inBlock, byte *outBlock) const
{
e.ProcessBlock(inBlock, outBlock);
d.ProcessBlock(outBlock);
e.ProcessBlock(outBlock);
}
void DES_EDE_Decryption::ProcessBlock(byte *inoutBlock) const
{
d.ProcessBlock(inoutBlock);
e.ProcessBlock(inoutBlock);
d.ProcessBlock(inoutBlock);
}
void DES_EDE_Decryption::ProcessBlock(const byte *inBlock, byte *outBlock) const
{
d.ProcessBlock(inBlock, outBlock);
e.ProcessBlock(outBlock);
d.ProcessBlock(outBlock);
}
void TripleDES_Encryption::ProcessBlock(byte *inoutBlock) const
{
e1.ProcessBlock(inoutBlock);
d.ProcessBlock(inoutBlock);
e2.ProcessBlock(inoutBlock);
}
void TripleDES_Encryption::ProcessBlock(const byte *inBlock, byte *outBlock) const
{
e1.ProcessBlock(inBlock, outBlock);
d.ProcessBlock(outBlock);
e2.ProcessBlock(outBlock);
}
void TripleDES_Decryption::ProcessBlock(byte *inoutBlock) const
{
d1.ProcessBlock(inoutBlock);
e.ProcessBlock(inoutBlock);
d2.ProcessBlock(inoutBlock);
}
void TripleDES_Decryption::ProcessBlock(const byte *inBlock, byte *outBlock) const
{
d1.ProcessBlock(inBlock, outBlock);
e.ProcessBlock(outBlock);
d2.ProcessBlock(outBlock);
}
NAMESPACE_END
openssl å¦ä½ä½¿ç¨
为ä¸ä¸ªåºäºå¯ç å¦çå®å ¨å¼åå ï¼OpenSSLæä¾çåè½ç¸å½å¼ºå¤§åå ¨é¢ï¼åæ¬äºä¸»è¦çå¯ç ç®æ³ã常ç¨çå¯é¥åè¯ä¹¦å°è£ 管çåè½ä»¥åSSLåè®®ï¼å¹¶æä¾äºä¸°å¯çåºç¨ç¨åºä¾æµè¯æå ¶å®ç®ç使ç¨ã
1.对称å å¯ç®æ³
OpenSSLä¸å ±æä¾äº8ç§å¯¹ç§°å å¯ç®æ³ï¼å ¶ä¸7ç§æ¯åç»å å¯ç®æ³ï¼ä» æçä¸ç§æµå å¯ç®æ³æ¯RC4ãè¿7ç§åç»å å¯ç®æ³åå«æ¯AESãDESãBlowfishãCASTãIDEAãRC2ãRC5ï¼é½æ¯æçµåå¯ç æ¬æ¨¡å¼ï¼ECBï¼ãå å¯åç»é¾æ¥æ¨¡å¼ï¼CBCï¼ãå å¯åé¦æ¨¡å¼ï¼CFBï¼åè¾åºåé¦æ¨¡å¼ï¼OFBï¼åç§å¸¸ç¨çåç»å¯ç å å¯æ¨¡å¼ãå ¶ä¸ï¼AES使ç¨çå å¯åé¦æ¨¡å¼ï¼CFBï¼åè¾åºåé¦æ¨¡å¼ï¼OFBï¼åç»é¿åº¦æ¯ä½ï¼å ¶å®ç®æ³ä½¿ç¨çåæ¯ä½ãäºå®ä¸ï¼DESç®æ³éé¢ä¸ä» ä» æ¯å¸¸ç¨çDESç®æ³ï¼è¿æ¯æä¸ä¸ªå¯é¥å两个å¯é¥3DESç®æ³ã
2.é对称å å¯ç®æ³
OpenSSLä¸å ±å®ç°äº4ç§é对称å å¯ç®æ³ï¼å æ¬DHç®æ³ãRSAç®æ³ãDSAç®æ³åæ¤åæ²çº¿ç®æ³ï¼ECï¼ãDHç®æ³ä¸è¬ç¨æ·å¯é¥äº¤æ¢ãRSAç®æ³æ¢å¯ä»¥ç¨äºå¯é¥äº¤æ¢ï¼ä¹å¯ä»¥ç¨äºæ°åç¾åï¼å½ç¶ï¼å¦æä½ è½å¤å¿åå ¶ç¼æ ¢çé度ï¼é£ä¹ä¹å¯ä»¥ç¨äºæ°æ®å å¯ãDSAç®æ³åä¸è¬åªç¨äºæ°åç¾åã
3.ä¿¡æ¯æè¦ç®æ³
OpenSSLå®ç°äº5ç§ä¿¡æ¯æè¦ç®æ³ï¼åå«æ¯MD2ãMD5ãMDC2ãSHAï¼SHA1ï¼åRIPEMDãSHAç®æ³äºå®ä¸å æ¬äºSHAåSHA1两ç§ä¿¡æ¯æè¦ç®æ³ï¼æ¤å¤ï¼OpenSSLè¿å®ç°äºDSSæ åä¸è§å®ç两ç§ä¿¡æ¯æè¦ç®æ³DSSåDSS1ã
4.å¯é¥åè¯ä¹¦ç®¡ç
å¯é¥åè¯ä¹¦ç®¡çæ¯PKIçä¸ä¸ªéè¦ç»æé¨åï¼OpenSSL为ä¹æä¾äºä¸°å¯çåè½ï¼æ¯æå¤ç§æ åã
é¦å ï¼OpenSSLå®ç°äºASN.1çè¯ä¹¦åå¯é¥ç¸å ³æ åï¼æä¾äºå¯¹è¯ä¹¦ãå ¬é¥ãç§é¥ãè¯ä¹¦è¯·æ±ä»¥åCRLçæ°æ®å¯¹è±¡çDERãPEMåBASEçç¼è§£ç åè½ãOpenSSLæä¾äºäº§çåç§å ¬å¼å¯é¥å¯¹å对称å¯é¥çæ¹æ³ãå½æ°ååºç¨ç¨åºï¼åæ¶æä¾äºå¯¹å ¬é¥åç§é¥çDERç¼è§£ç åè½ã并å®ç°äºç§é¥çPKCS#åPKCS#8çç¼è§£ç åè½ãOpenSSLå¨æ åä¸æä¾äºå¯¹ç§é¥çå å¯ä¿æ¤åè½ï¼ä½¿å¾å¯é¥å¯ä»¥å®å ¨å°è¿è¡åå¨åååã
å¨æ¤åºç¡ä¸ï¼OpenSSLå®ç°äºå¯¹è¯ä¹¦çX.æ åç¼è§£ç ãPKCS#æ ¼å¼çç¼è§£ç 以åPKCS#7çç¼è§£ç åè½ã并æä¾äºä¸ç§ææ¬æ°æ®åºï¼æ¯æè¯ä¹¦ç管çåè½ï¼å æ¬è¯ä¹¦å¯é¥äº§çã请æ±äº§çãè¯ä¹¦ç¾åãåéåéªè¯çåè½ã
äºå®ä¸ï¼OpenSSLæä¾çCAåºç¨ç¨åºå°±æ¯ä¸ä¸ªå°åçè¯ä¹¦ç®¡çä¸å¿ï¼CAï¼ï¼å®ç°äºè¯ä¹¦ç¾åçæ´ä¸ªæµç¨åè¯ä¹¦ç®¡çç大é¨åæºå¶ã
5.SSLåTLSåè®®
OpenSSLå®ç°äºSSLåè®®çSSLv2åSSLv3ï¼æ¯æäºå ¶ä¸ç»å¤§é¨åç®æ³åè®®ãOpenSSLä¹å®ç°äºTLSv1.0ï¼TLSæ¯SSLv3çæ ååçï¼è½ç¶åºå«ä¸å¤§ï¼ä½æ¯ç«æå¾å¤ç»èä¸å°½ç¸åã
è½ç¶å·²ç»æä¼å¤ç软件å®ç°äºOpenSSLçåè½ï¼ä½æ¯OpenSSLéé¢å®ç°çSSLåè®®è½å¤è®©æ们对SSLåè®®æä¸ä¸ªæ´å æ¸ æ¥ç认è¯ï¼å 为è³å°åå¨ä¸¤ç¹ï¼ä¸æ¯OpenSSLå®ç°çSSLåè®®æ¯å¼æ¾æºä»£ç çï¼æ们å¯ä»¥è¿½ç©¶SSLåè®®å®ç°çæ¯ä¸ä¸ªç»èï¼äºæ¯OpenSSLå®ç°çSSLåè®®æ¯çº¯ç²¹çSSLåè®®ï¼æ²¡æè·å ¶å®åè®®ï¼å¦HTTPï¼åè®®ç»åå¨ä¸èµ·ï¼æ¾æ¸ äºSSLåè®®çæ¬æ¥é¢ç®ã
6.åºç¨ç¨åº
OpenSSLçåºç¨ç¨åºå·²ç»æ为äºOpenSSLéè¦çä¸ä¸ªç»æé¨åï¼å ¶éè¦æ§æææ¯OpenSSLçå¼åè å¼å§æ²¡ææ³å°çãç°å¨OpenSSLçåºç¨ä¸ï¼å¾å¤é½æ¯åºäºOpenSSLçåºç¨ç¨åºèä¸æ¯å ¶APIçï¼å¦OpenCAï¼å°±æ¯å®å ¨ä½¿ç¨OpenSSLçåºç¨ç¨åºå®ç°çãOpenSSLçåºç¨ç¨åºæ¯åºäºOpenSSLçå¯ç ç®æ³åºåSSLåè®®åºåæçï¼æ以ä¹æ¯ä¸äºé常好çOpenSSLçAPI使ç¨èä¾ï¼è¯»æææè¿äºèä¾ï¼ä½ 对OpenSSLçAPI使ç¨äºè§£å°±æ¯è¾å ¨é¢äºï¼å½ç¶ï¼è¿ä¹æ¯ä¸é¡¹é»ç¼ä½ çæå¿åçå·¥ä½ã
OpenSSLçåºç¨ç¨åºæä¾äºç¸å¯¹å ¨é¢çåè½ï¼å¨ç¸å½å¤ç人çæ¥ï¼OpenSSLå·²ç»ä¸ºèªå·±å好äºä¸åï¼ä¸éè¦ååæ´å¤çå¼åå·¥ä½äºï¼æ以ï¼ä»ä»¬ä¹æè¿äºåºç¨ç¨åºæ为OpenSSLçæ令ãOpenSSLçåºç¨ç¨åºä¸»è¦å æ¬å¯é¥çæãè¯ä¹¦ç®¡çãæ ¼å¼è½¬æ¢ãæ°æ®å å¯åç¾åãSSLæµè¯ä»¥åå ¶å®è¾ å©é ç½®åè½ã
7.Engineæºå¶ Engineæºå¶çåºç°æ¯å¨OpenSSLç0.9.6ççäºæ ï¼å¼å§çæ¶åæ¯å°æ®éçæ¬è·æ¯æEngineççæ¬åå¼çï¼å°äºOpenSSLç0.9.7çï¼Engineæºå¶éæå°äºOpenSSLçå æ ¸ä¸ï¼æ为äºOpenSSLä¸å¯ç¼ºå°çä¸é¨åã Engineæºå¶ç®çæ¯ä¸ºäºä½¿OpenSSLè½å¤éæå°ä½¿ç¨ç¬¬ä¸æ¹æä¾ç软件å å¯åºæè 硬件å å¯è®¾å¤è¿è¡å å¯ãOpenSSLçEngineæºå¶æåå°è¾¾å°äºè¿ä¸ªç®çï¼è¿ä½¿å¾OpenSSLå·²ç»ä¸ä» ä» ä½¿ä¸ä¸ªå å¯åºï¼èæ¯æä¾äºä¸ä¸ªéç¨å°å å¯æ¥å£ï¼è½å¤ä¸ç»å¤§é¨åå å¯åºæè å å¯è®¾å¤åè°å·¥ä½ãå½ç¶ï¼è¦ä½¿ç¹å®å å¯åºæå å¯è®¾å¤æ´OpenSSLåè°å·¥ä½ï¼éè¦åå°éçæ¥å£ä»£ç ï¼ä½æ¯è¿æ ·çå·¥ä½é并ä¸å¤§ï¼è½ç¶è¿æ¯éè¦ä¸ç¹å¯ç å¦çç¥è¯ãEngineæºå¶çåè½è·Windowsæä¾çCSPåè½ç®æ æ¯åºæ¬ç¸åçãç®åï¼OpenSSLç0.9.7çæ¬æ¯æçå åµç¬¬ä¸æ¹å å¯è®¾å¤æ8ç§ï¼å æ¬ï¼CryptoSwiftãnCipherãAtallaãNuronãUBSECãAepãSureWare以åIBM CCAç硬件å å¯è®¾å¤ãç°å¨è¿åºç°äºæ¯æPKCS#æ¥å£çEngineæ¥å£ï¼æ¯æ微软CryptoAPIçæ¥å£ä¹æ人è¿è¡å¼åãå½ç¶ï¼ææä¸è¿°Engineæ¥å£æ¯æä¸ä¸å®å¾å ¨é¢ï¼æ¯å¦ï¼å¯è½æ¯æå ¶ä¸ä¸ä¸¤ç§å ¬å¼å¯é¥ç®æ³ã
8.è¾ å©åè½
BIOæºå¶æ¯OpenSSLæä¾çä¸ç§é«å±IOæ¥å£ï¼è¯¥æ¥å£å°è£ äºå ä¹ææç±»åçIOæ¥å£ï¼å¦å å访é®ãæ件访é®ä»¥åSocketçãè¿ä½¿å¾ä»£ç çéç¨æ§å¤§å¹ 度æé«ï¼OpenSSLæä¾APIçå¤ææ§ä¹éä½äºå¾å¤ã
OpenSSL对äºéæºæ°ççæå管çä¹æä¾äºä¸æ´å¥ç解å³æ¹æ³åæ¯æAPIå½æ°ãéæºæ°ç好åæ¯å³å®ä¸ä¸ªå¯é¥æ¯å¦å®å ¨çéè¦åæã
OpenSSLè¿æä¾äºå ¶å®çä¸äºè¾ å©åè½ï¼å¦ä»å£ä»¤çæå¯é¥çAPIï¼è¯ä¹¦ç¾åå管çä¸çé ç½®æ件æºå¶ççãå¦æä½ æ足å¤çèå¿ï¼å°ä¼å¨æ·±å ¥ä½¿ç¨OpenSSLçè¿ç¨æ ¢æ ¢åç°å¾å¤è¿æ ·çå°åè½ï¼è®©ä½ ä¸æææ°çæåã
什么是国密算法?
国密算法,由我国国家密码管理局发布的密码算法标准,旨在确保国家信息安全。目前,我国已发布包括SM1、SM2、网易狼人杀源码SM3、SM4、SM7、SM9以及祖冲之密码算法(ZUC)在内的国产商用密码标准算法,广泛应用于金融、电子政务及安防等关键领域。制作java源码通过使用国密算法,可对敏感数据进行机密性、完整性和可用性保护,同时减少对外部密码产品的依赖,显著提升国家信息安全水平。
国密算法的产生背景主要在于对网络信息传输和存储过程中数据保密性和安全性的迫切需求。由于传统国际标准加密算法存在源代码安全性问题,中国为构建安全的行业网络环境并增强国家行业信息系统的“安全可控”能力,自年开始积极研发国密算法,年正式发布。多年来,LY影视源码国密算法在持续改进和完善后,已成为中国自主研发的核心密码算法,广泛应用于各行各业,显著提升了中国在密码技术领域的核心竞争力。
国密算法具有高度的安全性、高效性和灵活性。它采用了复杂且严密的密码学原理,能够有效抵抗各种传统和现代密码攻击。同时,国密算法注重效率,加密速度和运行效率较高,油烟 平台 源码适应不同密钥长度的需求。此外,其标准化程度高,符合国际密码学标准,且在国内应用广泛,成为信息安全领域的基础核心算法之一。
国密算法的自主创新特性意味着中国可以独立掌控算法的实现和推广,减少对外部依赖,提升自主抵抗能力。国密算法适用于金融、电子商务、政采源码通信、物联网、区块链等多领域,确保数据在不同场景下的安全保护。
国密算法主要通过SM1(SCB2)、SM2、SM3、SM4、SM7、SM9和祖冲之密码算法(ZUC)等实现和应用。其中,SM1、SM4、SM7、ZUC属于对称加密算法;SM2、SM9属于非对称算法;SM3则为杂凑算法。接下来,将详细阐述国密算法中常用算法的实现和应用。
SM1算法主要应用于小数据量的加密保护,广泛应用于智能IC卡、智能密码钥匙、门禁卡、加密卡等安全产品。
SM2算法基于椭圆曲线加密技术,包括了数字签名、密钥协商和数据加密等功能,广泛应用于电子商务、互联网金融、物联网等多个领域,确保用户信息和交易的安全性。
SM3算法作为摘要算法,通过哈希函数将任意长度的消息压缩成固定长度的摘要,用于数字签名、数据完整性检测及消息验证。在密码学协议、数字证书和电子签名等领域提供完整性、真实性和来源验证。
SM4算法为分组对称加密算法,实现公开,适用于大数据量的加密和解密,如静态存储或数据信号传输通道中数据的加解密,确保网络传输和存储的敏感数据安全。
国密算法支持多种分组模式,包括ECB和CBC模式,ECB模式实现简单,各段数据间互不影响;而CBC模式安全性高于ECB,但明文块不能并行计算,且误差会传递下去。
在实际应用中,国密算法与AD-WAN技术结合,应用于IP/MPLS纵向网场景,构建国密数据加密通道,实现IPsec隧道保护。同时,国密算法在4G/5G VPDN业务组网中,与L2TP和IPsec技术结合,确保接入安全和通信数据安全。这些应用充分体现了国密算法在保障国家信息安全方面的重要作用。
比特源码app_比特币源码下载
移动端社区app源码_移动端社区app源码是什么

leg乐游棋牌源码_leg乐游棋牌贴吧

卖菜软件源码可打折_卖菜软件定制

源码app打包

小米4官网源码